
Diana Riba
Infected with Pegasus
Member of the European Parliament, ERC (2019 - present)


Over 200 texts like this are part of one of Europe’s largest-known cases of state-run phone hacking. Simply clicking the link would infect a phone with highly sophisticated spyware.
This is the story of secret hacking capabilities, how a government used them, and the threat they pose to fundamental rights and democracy.
What if clicking doesn’t matter?
Many more victims were hacked silently, through “zero-click” vulnerabilities. No malicious links. No trickery. One moment, a victim’s phone was safe; the next, it was silently transmitting their private information to government spies.
Beginning in 2017, and possibly as early as 2015, Catalan citizens’ phones were targeted by a large-scale operation using spyware from the mercenary surveillance firm NSO Group.
That wasn’t all.
Other Catalans’ computers were being targeted and infected with spyware made by another mercenary surveillance firm: Candiru.
Both companies claim that their products are only intended to fight serious crime and terrorism, and are sold exclusively to governments.


Spain has had a conflictual relationship with Catalonia for many years. Tensions reached a tipping point during the 2017 Catalan independence referendum, which was found to be unconstitutional by the Constitutional Court of Spain. The result? The dissolving of the Catalan parliament, exile of several prominent politicians, and a Supreme Court trial that led to the conviction and sentencing of nine Catalan leaders to prison, who were subsequently pardoned.


At least 65 individuals were infected or targeted with sophisticated spyware, and have consented to tell their stories.
The spyware covertly penetrates mobile phones (and other devices) and is capable of reading texts, listening to calls, collecting passwords, tracking locations, accessing the target device's microphone and camera, and harvesting information from apps. Encrypted calls and chats can also be monitored. The technology can even maintain access to victims’ cloud accounts after the infection has ended.
Its name?
It’s a sophisticated piece of government exclusive-spyware tied to hundreds of abuses around the world.
You may have heard of Pegasus. It’s a sophisticated mercenary spyware sold to governments around the world. It has been tied to hundreds of cases of abuse. Some of the worst cases have occurred at the hands of authoritarian regimes in Saudi Arabia, the United Arab Emirates, Togo, Jordan, and many others.
Most prominently, Pegasus was employed against family members of Saudi Arabian journalist Jamal Khashoggi before and after he was murdered in Turkey. It has been used against journalists around the world, as well as human rights defenders, dissidents, and truth tellers.
Still other abuses have happened at the hands of purported democracies like India, Poland, Hungary, and El Salvador.
Catalans weren’t just targeted with Pegasus. Here’s how we caught Candiru.

In idyllic Girona, Joan Matamala was at his office, working on his computer. He didn’t know it yet, but we’d just discovered that his device was infected. It was time for immediate action. After a flurry of calls, we reached his colleagues. Fabricating an excuse, they asked him to step into the hallway. The ruse was necessary. The infected device might be listening. Once he consented, his computer was immediately securely packaged and rushed through the night for forensic analysis.
We’d just caught a live copy of Candiru.
Spyware like Candiru is designed to self-destruct and hide its traces. Catching a live infection is difficult, but having the actual code is essential to understanding and neutralizing it.
Once we had the sample, we worked with Microsoft to investigate. They identified two zero-day vulnerabilities that Candiru used to infect Windows devices with spyware they codenamed DevilsTongue.
On July 13, 2021, Microsoft updated all 1.4 billion Windows devices with a patch that prevented further Candiru infections using these two vulnerabilities.

Was the large-scale hacking of Catalonia’s political & civil society appropriate?
Most would agree that spying on counterparts during a political negotiation process is an act of bad faith.
People’s views on Catalan independence differ, but many of the hacking victims have never been charged or convicted of criminal activity for their political activism. They are advocates, politicians, nonprofit leaders, lawyers, journalists, and even open-source software developers working on democratic participation. They include Catalan Presidents, legislators, and Members of the European Parliament. In some cases, family members were also infected.
The targeting occurred during political negotiations and debate over Catalan independence. Most would agree that spying on counterparts during a political negotiation process is an act of bad faith.
Meet some of the targets
Pegasus and Candiru were used to hack Catalans from many parts of society.
Four Catalan Members of the European Parliament (MEP) that supported independence were targeted with Pegasus, or indirectly via relational targeting. Two MEPs’ devices were hacked, one after they had assumed office and the other shortly before being substituted into the role. The Parliamentary staff, family members or close associates of two further MEPs were also targeted for hacking.

Member of the European Parliament, ERC (2019 - present)

Member of the European Parliament, ERC (2020 - present)
Former Member of the Parliament of Catalonia (2012 - 2015)
Infected shortly before being substituted into the role.

Member of the European Parliament, JUNTS (2020 - present)
Former Minister of Education of Catalonia (2017 - 2017)

Member of the European Parliament, JUNTS (2019 - present)
Former President of Catalonia (2016 - 2017)
People at multiple Catalan civil society organizations were targeted with Pegasus or Candiru. These included Omnium Cultural and Assemblea Nacional Catalana, two organizations that support Catalan independence. So were lawyers representing prominent Catalans. Several well-known open-source developers working on software projects related to democratic participation and decentralization were also targeted.
President ANC (Since 2018)

Former President ANC (2015 - 2017)

Journalist. Spouse of Omnium’s former president Jordi Cuixart.

Former Vice President, Omnium (2017 - 2022)

Lawyer representing multiple prominent Catalans

Lawyer representing multiple prominent Catalans

Lawyer representing multiple prominent Catalans

Lawyer representing multiple prominent Catalans

Technology Lead, Polygon

CTO Aragon Labs.
Co-founder, Vocdoni

Co-founder, Vocdoni
Every Catalan president since 2010 was targeted with Pegasus, either while serving their term, before they were elected, or after retiring. In addition, the leadership and members of Catalan legislative bodies were extensively targeted, including multiple presidents of the Catalan parliament either while in office, or prior to taking office. A wide range of legislators from Catalan political parties were also targeted.

(infected while serving as VP during Torra’s Presidency)
President. Date Served: 2021-present

(infected while in office)
Former President. Date Served: 2018-2020

(relational targeting)
Former President. Date Served: 2016-2017

(infected after leaving office)
Former President. Date Served: 2010-2015

(targeted while in office)
Former President of the Parliament of Catalonia

(targeted while a member of the Spanish Congress)
President of Catalan parliament

(Junts per Catalunya, JUNTS) - (11 members targeted)

(Esquerra Republicana de Catalunya, ERC) - (12 members targeted)
(Candidatura d'Unitat Popular, CUP) - (4 members targeted)

(Partit Demòcrata Europeu Català, PDeCAT) - (3 members targeted)

(Partit Nacionalista Català, PNC) - (1 member targeted)


Elisenda is a prominent Catalan economist, academic, and activist. She was working from home during the COVID lockdown when the first infection attempt arrived. It purported to be a news story about the Catalan National Assembly.
On the 10th of June she was running for a board seat with the Catalan National Assembly. Online voting had just begun when a second infection attempt arrived. It masqueraded as a Twitter update from a Catalan newspaper.
Forensic evidence also confirms that Elisenda was infected with Pegasus on or around October 29, 2019. The targeting took place during a period of protest against the sentencing of several prominent Catalan political figures.

Forensic evidence was not available to confirm whether the former Catalan President was infected with Pegasus. However, we surmise he may have been the focal point for extensive surveillance through relational targeting.
We found an arc of targeting around the former president. At least eleven individuals were targeted with Pegasus, ranging from his spouse and residence staff to confidants, his lawyer, and friends. Taken together, monitoring from their devices would have provided a detailed window into his life, movements, and thinking.
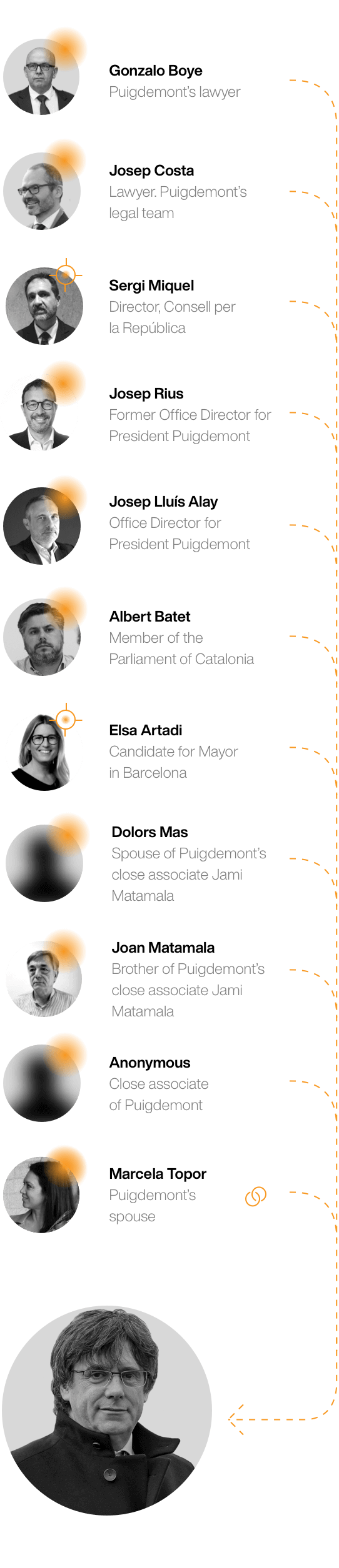


Gonzalo Boye is a lawyer who has represented numerous Catalan political figures including Presidents Puigdemont and Torra, as well as many other high profile Catalans. His targeting raises concerning questions about the possibility that lawyer-client privilege was deliberately violated.
Between January and May 2020, Gonzalo was targeted at least 18 times with Pegasus infection attempts via SMS. Some of the messages masqueraded as tweets from organizations like Human Rights Watch, The Guardian, Columbia Journalism Review, and Politico.
A forensic analysis found evidence that Boye’s phone had an active Pegasus infection as of October 30, 2020. The timing is interesting: one of his clients had been arrested just 48 hours before the infection.
Image: “Declaració de Quim Torra al TSJC” © Òmnium Cultural. From Wikimedia Commons.
People think that the problem with mercenary spyware is that it is sold to dictators who abuse it. True.
But even when spyware like Pegasus is sold to democracies, it gets abused: democracies like Poland, Mexico, El Salvador, and India have all had abuse scandals. Troublingly, the cases often coincide with democratic backsliding.
Once secret spyware is purchased, it’s not a question of whether abuse will happen, but when. Even in a democracy.